SAP Security Monitoring & Incident Response Management
for SAP Enterprise Threat Detection
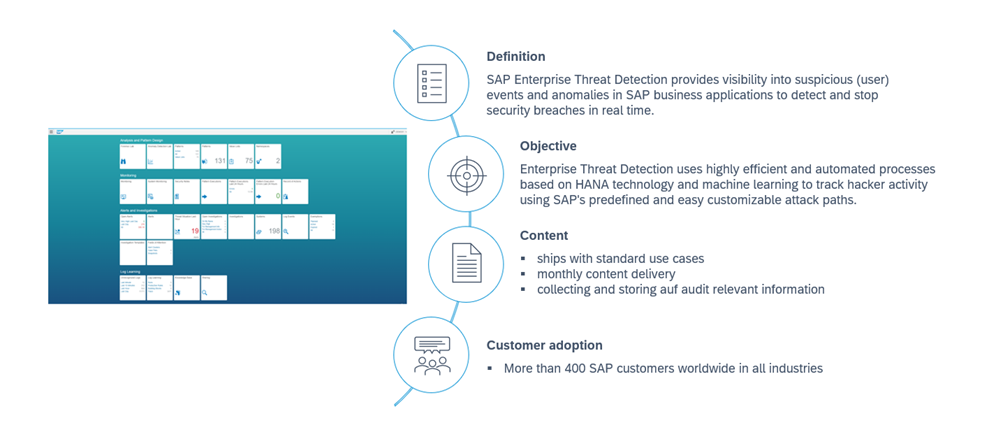
Organizations are facing an increasing number of cyberattacks against their SAP systems, most of the times without even knowing that their data had been compromised. The most effective protection is implementing a SAP Security Monitoring and Incident Response process to be able to identify and mitigate vulnerabilities before they even can be exploited.
Cyberattacks have been rated as one of the Top 5 risks in “The Global Risks Report 2020” by the World Economic Forum, continuing to grow as IoT cyberattacks alone are expected to double by 2025. As a result of the COVID-19 pandemic almost every industry had to implement new solutions quickly (e.g., remote accesses), giving attackers an even bigger surface to act on.
Research states that companies have a big need for action since the rate of detection is only around 0.05%. This means that most of the cyberattacks remain unnoticed, giving hackers plenty of time to explore the landscape and to obtain the data they are looking for. A slow response to a data breach can cause even more trouble for your organization, resulting in a loss of customer trust, productivity, or regulatory fines.
What customers say about our Managed Security Service for SAP Enterprise Threat Detection
In this session, you can learn how we run SAP Enterprise Threat Detection (ETD) on a day-to-day basis for SAP SE, how we implement regulatory requirements, and how we set up an effective response to critical system activities.
Managed Security Service for SAP Enterprise Threat Detection
To protect your SAP assets from cyberattacks, we provide advanced services for SAP Security Monitoring & Incident Response Management with SAP Enterprise Threat Detection (ETD):
- Development of a Target Operating Model
- SAP Security Monitoring: Operative monitoring of SAP ETD (up to 24/7)
- Development of new patterns (use-cases)
- Training (Classroom training / workshops)
- Advisory and support for mitigation of vulnerabilities
- Forensics analysis
Development of a Target Operating Model
Before the Go-Live, there is a ramp-up phase to create a Target Operating Model (TOM). The main purpose of the Target Operating Model is to define how the processes for SAP ETD can be best organized to implement SAP Security Monitoring and Incident Response Management efficiently and effectively, integrating them into existing processes. The following components are part of the TOM:
- Definition of Service-Level Agreements (SLAs)
- Definition of responsibilities
- Development of the ticketing process
- Workflow descriptions for alerts & investigations (Standard Operating Procedures)
- Review of architecture and set-up
- Comparison of patterns in existing tools (F-Run, Splunk, etc.)
- Sizing and identification of potential savings
SAP Security Monitoring and SIEM-integration
SAP Security Monitoring is a living process that we operate on a permanent basis. With our specialized monitoring and incident response team, we are able discover threats or suspicious activity (events) inside your SAP landscape and take countermeasures to protect your most valuable business assets – your data.
Alerting
Through continuous monitoring with SAP Enterprise Threat Detection (SAP ETD), our SAP security specialists analyze the events (alerts) provided by SAP ETD and assess whether they are authorized accesses or possible security incidents that require countermeasures. Response time is key for us. After the alert has been received by our SAP Security Monitoring Team, process automations come into play, which will be developed during the project based on the history (number of alerts per use case). The development of process automations is an integral part in our way of working in order to avoid as many manual steps as possible.
As a simple example of process automation, alerts indicating a new assignment of SAP_ALL to a user automatically generate a ticket in ServiceNow (or other ticketing systems). Background: SAP_ALL should not be assigned to any user (except temporarily to a Firefighter-User). The same principle applies to the DEBUG & REPLACE authorization in production, to give another example. Throughout our activities, we will develop numerous such process automations to reduce manual processing times and efforts.
To successfully integrate SAP Security Monitoring into your IT security processes, we can integrate SAP ETD into your SIEM (Security Information and Event Management) system and build the bridge to your SOC (Security Operation Center). By contributing our SAP Security & Compliance expertise, we are a valuable addition for your SOC to cover all security specifics that come with SAP technology.
Investigations
The key for a successful incident response management is having the right process in place, ideally, enabling the team members to take immediate countermeasures if necessary. The Initial categorization and prioritization of incidents is a critical step for determining how the incident will be handled and how much time is available for its resolution. Following our best practice approach, our incident response management process can be summarized as follows:
Step 1: Analysis of the alerts
In the first step, the alert in SAP ETD is examined and evaluated to decide whether to create a ticket directly in ServiceNow (or other ticketing systems) or if further investigations are necessary first. All alerts are logged and tracked, providing a comprehensive historical record that offers meaningful insights into all discovered events / alerts.
Step 2: Categorization and prioritization of alerts
The alerts are automatically categorized in order of their criticality to determine the resolution time using automated ticketing rules, saving valuable time in the process. Assigning the correct priority to a ticket directly impacts the subsequent analysis process.
Step 3: Assignment of investigations and creation of tasks
Once the alert is categorized and prioritized, it is assigned to one of our SAP security specialists with the relevant expertise. Depending on the complexity of the incident, countermeasures can be divided into sub-activities or tasks if further investigation requires different expertise from multiple specialists.
Step 4: SLA-Management and escalation
The response and resolution time are defined in a SLA (Service Level Agreement) that serves as a guideline to ensure that alerts and investigations are processed according to the agreed conditions. If an SLA is violated, we escalate the incident to ensure a fast and prioritized resolution in a collaborative approach with your IT security organization.
Step 5: Completion of the investigation
We consider an investigation resolved once our SAP security specialists have completed the analysis and ideally found a permanent solution to prevent similar incidents in the future. The resolution of the incident is documented in the ServiceNow ticketing system, and all relevant parties are informed. The incident is closed in the ServiceNow ticketing system once the issue is resolved, and the solution has been accepted by the responsible persons.
Review after the investigation
After an investigation is concluded, it is our best practice to document all steps taken to resolve the incident and prevent recurrence (where possible). Post-incident review support the organization in preparing it for future incidents following similar scenarios, leading to reduced resolution times and more effective responses. Through review and documentation, further automations can be developed to standardize the approach for similar incidents.
Development of new patterns (use-cases)
The continuous development of SAP Enterprise Threat Detection is a central component of our Managed Security Service. During the ramp-up phase, selected patterns are developed as needed by smarterSec and gradually put into production. The goal is to collaborate with the customer during the ramp-up phase to gather valuable insights into the expected efforts, which can be considered when deploying additional patterns.
The documentation of the use-cases is conducted by smarterSec. This includes the evaluation, documentation, and description of the workflow for each newly developed use-case. The documentation and workflow description of the use-cases are created according to the customer’s specifications (layout) and serve the purpose of tracing the individual investigation steps and applications.
After the ramp-up phase, smarterSec will continue to develop additional patterns continuously, if requested by the customer. The individual patterns will be put into production directly or applied at a later time, depending on the analysis of the efforts involved, in order to manage the load accordingly.
Our team has already developed numerous market-leading SAP Security software solutions and possesses a strong expertise in SAP Security product development, including test case development.
Training (Classroom training / workshops)
After initiating the continuous operation of SAP Enterprise Threat Detection and implementing & documenting the defined processes, various training sessions can be conducted for selected employees. The creation of training materials and preparation of the training sessions are handled by smarterSec. The training materials are developed in the specified format (layout) and are subsequently used as an internal training course for the client. The training sessions will provide participants with fundamental knowledge on the following topics:
Architecture
- What is the structure of SAP and what opportunities does it offer?
- How is SAP Enterprise Threat Detection implemented and configured?
- What additional possibilities do standard integrations offer (e.g., in splunk)?
Security Monitoring & Incident-Response-Management
- How is a pattern structured?
- What is an alert and how is it handled?
- What measures are taken for different alerts?
- How are actions created and managed in the ServiceNow ticketing system?
- What does the incident response process look like? (for selected patterns)
- How are incidents and forensic investigations reported?
- How can a recurrence of the incident be prevented in the future?
Training courses from the SAP Security Training Catalog, such as WDESA3, have been conducted and set up by our SAP Security consultants. This experience allows us to demonstrate our proficiency in conducting training sessions with and for SAP.
Advisory and support for mitigation of vulnerabilities
When our monitoring and incident response team discovers threats or suspicious activity, we act quickly to investigate and either work with you on thorough mitigation approaches or take over the mitigation completely. As part of our service, we advise your oranization on taking preventive measures and support the processes for reducing risks. In this way, we improve your security & compliance together every single day.
Forensic analysis
In case your organization had been a victim of a cyberattack, our forensics investigate and document the course, reasons, culprits, and consequences of the security incident or violation of rules of the organization or state laws. Through our experience with SAP attack vectors, we are often able to reconstruct the scenario and provide evidence for further legal action. The only way for organizations to defend themselves is to detect and respond with accuracy and speed.
Related topics: Managed Security Service for the smarterSec Security Platform // smarterSec Security Platform
Contact
smarterSec GmbH
Managed Security Service Provider for SAP®
Albert-Nestler-Str. 21, 76131 Karlsruhe, Germany
+49 (0) 721 160 800-0
info@smartersec.com
smarterSec APJ Pty Ltd.
Managed Security Service Provider for SAP®
Sydney, Australia
+61 (0) 419 000 723
info@smartersec.com
Follow Us on Social Media

