
What is DORA?
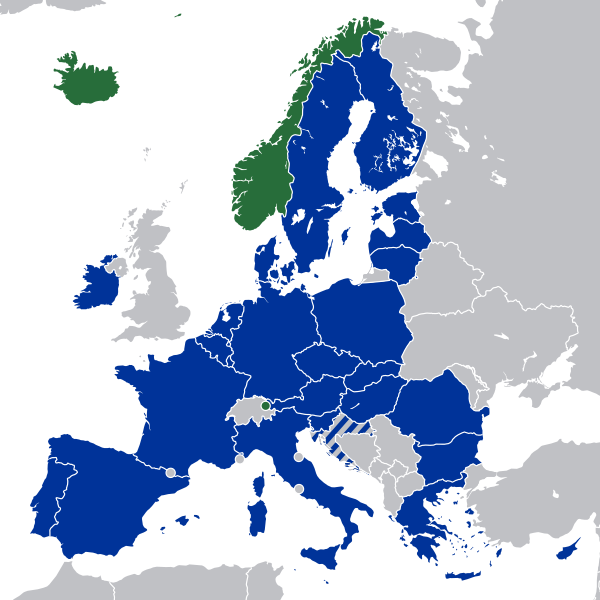
DORA, short for Digital Operational Resilience Act, is a regulation of the European Parliament in the financial sector and will be applied from January 2025. It addresses the topics of cyber security, ICT risks (Information and Communications Technology) and digital operational resilience and affects the European Economic Area (EEA). The EEA combines the European Union (EU, blue) and the European Free Trade Association (EFTA, green).
Is my company affected by DORA?
The DORA regulation applies to almost all companies in the financial sector, such as
- Credit Institutions
- Crypto-Asset Service Provider
- Trading Venues
- Crowdfunding Service Providers
- ICT Third-Party Service Providers
A complete list of every included and excluded entity can be found here.
What are the goals?
As digitalization progresses, the risks of cyberattacks and its consequences are increasing, which is why DORA aims to protect the companies’ assets and minimize the damage. Therefore, the following main objectives were defined:
- Standardizing national IT security regulations
- Strengthening the European financial market against cyberattacks
- Protecting the ICT services
- Ensuring digitale operational resilience
The main focus here is on digital operational resilience, in other words the ability of an organization to maintain business operations in the event of disruptions. This is to be realized in six different sectors:
ICT Risk Management
In this sector DORA intends to standardize the requirements across the entire financial sector so that the functionality of financial companies can be maintained or, if necessary, quickly restored.
DORA establishes an comprehensive and
well-documented internal governance and control framework that ensures appropriate management of ICT risks, including following elements:
- Detection and Identification
- Protection and Prevention
- Countermeasures and Recovery
Incident Response
A financial company is obliged to implement a management process that covers the following aspects:
- Appropriate handling of ICT-related incidents
- Monitoring and logging of ICT-related incidents
- Classification of the ICT-related incidents
- Reporting of ICT-related incidents
Incidents that are classified as severe are obliged to be reported to the relevant authority. To see which authority your company is assigned to, see Article 46 of DORA.
Testing
A financial company will be obliged to introduce a risk-based testing procedure for ICT. This includes tests such as:
- Pentests
- Network and physical security tests
- Scenario based tests
- Vulnerability assessments and scans
This determines whether or how well a company is prepared for an ICT incident and provides an overview of potential vulnerabilities.
Management of 3rd Party Risks
Potential risks of services and service providers must also be evaluated and monitored. With the help of a risk analysis, the financial company can assess the extent to which it is dependent on the third party and what risks could occur.
Additionally, there has to be an exit strategy for critical functions to ensure operational resilience.
Monitoring 3rd Party Service Provider
DORA also applies to third-party service providers, who are therefore also obliged to comply with the regulations.
The lead supervisory authority monitors whether the third-party service provider complies with the ICT risk management requirements.
The authority also makes recommendations that should be implemented by the service providers. If the third-party provider does not meet the essential requirements, the authorities can ask the financial companies to suspend the use of the service provider or even close it down completely.
Information Exchange
DORA encourages the cross-sector exchange of information and knowledge about threats that have occurred. This helps the supervisory authorities to develop crisis management and emergency exercises with scenarios for cyber attacks.
Where can smarterSec support your organization?
As a Managed Security Service Provider for SAP®, we are able to ensure the digital resilience of your SAP® systems in order to comply with DORA.
ICT Risk Management
The smarterSec Security Platform (SSP) monitors security-relevant activities in your SAP® system landscape. Thereby, SSP detects and identifies potential threats and provides instructions for mitigating risks.
Incident Response
To protect your SAP® assets from cyberattacks, we provide advanced services for SAP® Security Monitoring & Incident Response Management with SAP® Enterprise Threat Detection (ETD).
Testing
Our SAP® Security Assessment is a quick and easy way to efficiently test the current security and compliance level of one of your SAP® systems and have it assessed by our experienced SAP® Security & Compliance experts.
Management of 3rd Party Risks
The SAP® Security & Compliance Audit provides you a detailed overview of the risk level in your SAP® landscape. Every audit is by design customer specific and the exact efforts are depending on the detailed scope.
Further Information
To download the full DORA document, please follow this link. Further information can also be found on the official EU website EIOPA (European Insurance and Occupational Pensions Authority).