
Table of Contents
- What is UCON?
- Why should I implement UCON?
- How to setup and configure the UCON “RFC Basic Scenario”?
- How to maintain UCON?
- How can smarterSec provide support?
- Conclusion
What is UCON?
SAP introduced UCON (Unified Connectivity) as a security framework to manage, control, and secure external communication in SAP systems, with a particular focus on RFC (Remote Function Call) communication. UCON was developed with the primary objective of enhancing the security of SAP systems by managing the interaction between external systems or applications and SAP via RFC-enabled interfaces. RFCs are a common feature of SAP environments, facilitating communication between different SAP systems and external third-party systems.
The graphic below demonstrates how a user executes an RFM (remote-enabled function module) via RFC, enabling them to run applications from outside the system. The left side represents the course without UCON, while the right side shows the course with UCON activated.

Why should I implement UCON?
To resolve security issues in RFC communication
Many SAP systems have open or unsecured RFC interfaces, which creates a significant security risk, as unauthorized or malicious access via these open RFC connections could result in the compromise of sensitive business data or the disruption of critical processes. UCON was developed to address these risks by providing a solution to restrict and secure RFC communication.
To minimize the potential for system breaches
In earlier versions of SAP systems, all RFC-enabled function modules were typically accessible by default. This increased the risk of external attacks, such as the exploitation of unused or insecure interfaces. The introduction of UCON was designed to reduce the attack surface by allowing system administrators to disable unnecessary RFC interfaces and only permit essential communications.
To reinforce compliance with security standards
UCON enables organizations to meet the increasingly rigorous security standards and regulatory requirements (such as GDPR, SOX, etc.) that are in place. By enabling businesses to exercise greater control over external system access and communication, UCON is instrumental in facilitating compliance with corporate and legal security standards.
To transition from open RFC interfaces to controlled access
The introduction of UCON provides a centralized, controlled, and secure method to manage RFC connections, moving the system from a less-secure open interface setup to one where access is explicitly controlled and monitored.
How to setup and configure the UCON “RFC Basic Scenario”?
1. Configure the logging and evaluation phase
- Use transaction UCONCOCKPIT
- Under the tab “Unified Connectivity Scenario Selection” choose the scenario “RFC Basic Scenario”
- In the menu go via “More” to “Operations” and then to “Unified Conn. Customizing”
- Choose a suitable duration for the logging and evaluation phase (typically between 30-60 days)
2. Configure the UCON setup
- Use transaction UCONCOCKPIT
- Under the tab “Unified Connectivity Scenario Selection” choose the scenario “RFC Basic Scenario”
- In the menu go via “More” to “Operations” and then to “Unified Conn. Setup RFC Basic”
- Choose “Local” for the type of communication assembly
- Select if UCON should be activated for all clients or for the current client only
- Leave the checkbox “Transport RFC State Objects” deselected
3. Activate the UCON profile parameter
Activate UCON permanently (productive use):
- Call transaction RZ10.
- Select the profile for which the change shall be made.
- Under “Edit Profile” select “Extended maintenance” and click “Change”.
- Check if the parameter UCON/RFC/ACTIVE is already listed.
- If so, then change the value to “1”. If not, press “F5” to create a new parameter with said value.
- To save your changes, go back until you get to the report “Edit Profiles”, then click “Save”.
Activate UCON for testing purposes:
- Call transaction RZ11.
- Search for parameter UCON/RFC/ACTIVE.
- Click the button “Change Value” and insert the value “1”.
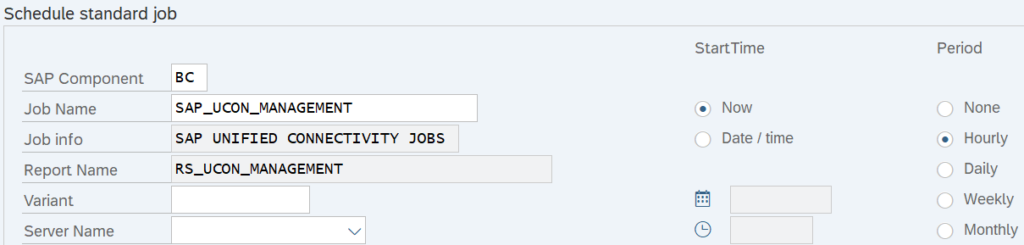
4. Schedule the UCON batch job
Batch jobs are tasks that are performed in the background without any user interactions. They are used to automate repetitive tasks such as report generation or data collection. The batch job SAP_UCON_MANAGEMENT is used to collect all RFC statistics. To schedule the UCON batch job, please follow these steps:
- Call transaction SM36.
- Press the button “Standard Jobs”.
- If no standard batch jobs are scheduled press the button “Default scheduling”.
- Add the SAP_UCON_MANAGEMENT batch job as shown below.
- Enter the desired start time and period.
- Save your changes.
How to maintain UCON?
Maintaining UCON is essential for ensuring that your SAP environment remains secure and efficient. Regular maintenance helps you to adapt to evolving business needs, manage security risks, and comply with regulatory requirements. Below are key strategies for an ongoing UCON maintenance:

Regular Monitoring
- UCON Cockpit: Utilize the UCON Cockpit (transaction UCONCOCKPIT) to continuously monitor all scenarios (RFC, Role Building, HTTP Allowlist). This tool allows you to track all external communications, identify unauthorized access attempts, and assess the performance of RFC calls.
- Analyze Logs: Regularly review logs generated during the logging phase to spot trends, anomalies, or unusual activity patterns. This proactive approach helps you detect potential security breaches early.
Periodic Audits
- Conduct Security Audits: Schedule regular audits of UCON settings, rules, and logs to ensure compliance with internal security policies and external regulations. This helps verify that access controls are effective and properly enforced.
- Review Security Policies: Regularly assess and update security policies based on audit findings and any changes in your organizational structure or business processes.
Review and Adjustments
- Evaluate Allowlists and Denielists: Periodically review the listed RFC-enabled function modules. Remove any obsolete entries and add new ones as business requirements change.
- Adjust Access Controls: As your organization evolves, adjust access controls to ensure that only authorized users and systems can communicate with the SAP environment.
System Updates
- Implement SAP Notes and Patches: Regularly check for and apply the latest SAP notes and security patches relevant to UCON. Keeping your system updated helps protect against vulnerabilities and enhances the functionality of UCON.
- Stay Informed on UCON Enhancements: Keep up-to-date of new features and improvements released by SAP for UCON and incorporate them into your system to take advantage of enhanced security measures.
User Awareness
- Train Staff: Provide regular training sessions for team members responsible for managing UCON. Ensure they understand best practices, new features, and how to respond to potential security incidents.
- Promote Security Awareness: Foster a culture of security awareness within your organization. Encourage users to report suspicious activity or potential security risks related to RFC communications.
Performance Optimization
- Analyze Performance Metrics: Regularly assess the performance of RFC calls to ensure that UCON is not adversely affecting system performance. Identify and resolve bottlenecks or inefficiencies in the RFC communication process.
- Adjust Logging Parameters: Based on performance assessments, adjust the duration and level of detail for logging as necessary to strike a balance between security and system performance.
Incident Response
- Establish an Incident Response Plan: Develop and maintain an incident response plan specifically for UCON-related security events. This should include procedures for investigating unauthorized access attempts or data breaches.
- Post-Incident Reviews: After a security incident, conduct a thorough review to identify lessons learned and adjust UCON configurations or policies to prevent recurrence.
How can smarterSec provide support?
Our smarterSec Security Platform (SSP) checks your UCON configurations, analyzes your logs for potential threats and scans for SAP Notes that are not implemented yet. Additionally we offer SAP Security Risk Assessments which is a quick and easy way to efficiently analyze the current security and compliance level of one of your SAP systems and have it assessed by our experienced SAP Security & Compliance experts.
Conclusion
Unified Connectivity (UCON) is a vital tool in SAP’s security arsenal, offering robust protection against unauthorized external access through RFC communications. Its quick setup and ease of use make it accessible for any organization looking to enhance their SAP security posture. By reducing the attack surface significantly, UCON ensures that critical business processes remain secure without disrupting daily operations. The phased implementation approach allows for careful evaluation before fully enforcing restrictions, and the continuous protection of both existing and newly introduced RFMs ensures long-term security.
In short, UCON simplifies the process of safeguarding SAP systems, making it an essential solution for mitigating cybersecurity risks in today’s digital landscape.
SAP documents about UCON:
- Unified Connectivity (UCON) – Overview
- UCON RFC Basic Scenario – Guide to Setup and Operations for SAP NetWeaver 740 SP5 (and higher)
Related Topics: smarterSec Security Platform // SAP Security Risk Assessments