
“May – The search for the evil character”
As part of the SAP Security patch day for the month of May, a total of 25 notes were published or updated. After downloading and checking the components, it turns out that only three of them are relevant and implementable on our SAP HCM system.
The note 33262101 addresses under vulnerability number CVE-2023-30743 Improper Neutralization of Input in SAPUI5. The described corrective action is simple: apply the latest patch for SAPUI5 – which is ultimately an exchange or upload of files to the system. In this fix, it does not allow a deeper analysis of the vulnerability and the applied fix.
The two notes 33159712 and 33159793 (vulnerability number CVE-2023-30742 and CVE-2023-29188) address a possible cross-site scripting (XSS) in the SAP CRM WebClient UI application. XSS – what was that? Right: Note 3293786 also concerned this vulnerability type; and at that time it was about the comparison between Input Validation and Output Encoding.
According to pure doctrine, output encoding – as context-specific matching of technically relevant characters – should be built in as a countermeasure for XSS. You may know this, if the expression Hello World<> results in either Hello World<> (for HTML content) or Hello%20World%3C%3E (for URLs). Such a conversion is achieved in ABAP programs, for example, using the ESCAPE command.
However, the above notes perform a kind of input validation by filtering out critical characters for an XSS attack:
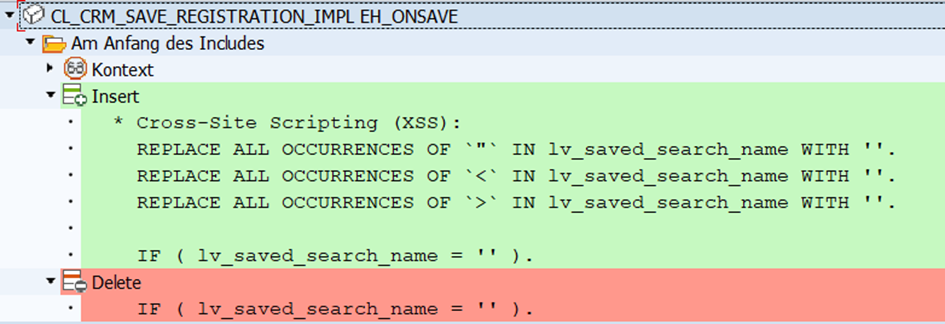
In principle, such filtering can also lead to success – the challenge is to make the filters complete and also catch all critical characters: what about the “‘”, for example? (single quotation mark) instead of the quotation marks? There is no limit to the creativity of the attackers – tip: google for the keyword “XSS Cheat Sheet”4.
But since in any case the validation increases the security and no functional deficits are possible, the notes were included (without any problems).
See you next time for the June patch day!
[1] https://launchpad.support.sap.com/#/notes/3326210
[2] https://launchpad.support.sap.com/#/notes/3315971