
SAP Security Patch Day 01/2022
A total of 9 notes were published by SAP in January1, with note 3131047 being the collective note for the fixes for the “log4shell” vulnerability – a total of 21 additional notes are referenced there (more on “log4shell” below).
Our process initially involves loading all security patches into the system via transaction SNOTE (or SAP Solution Manager). Then, all advisories are processed individually. This includes checking the advisories that have been marked as “not installable” by the system. The goal is to understand why the SAP note has this status, as well as to ensure that no other (manual) tasks are included in the textual description of the SAP note.
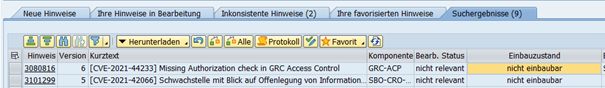
Using the example of note 3080816: the note provides a program correction for GRC Access Control. The related component GRC-ACP, in which the corrected objects are delivered, is not included in our system (since it is not a GRC system). Consequently, we can document our check and set the note to “not relevant”.
Only two notes are marked as installable in transaction SNOTE:
- 3112710: [CVE-2021-42067] Information Disclosure vulnerability in SAP NetWeaver Application Server for ABAP and ABAP Platform
- 3123196: [CVE-2021-44235] Code Injection vulnerability in utility class for SAP NetWeaver AS ABAP
After reviewing the advisory text, there is no specific impact on the HCM processes used. Both notes can therefore be imported directly and an additional regression test of the HCM application is not necessary. Note 3112710 on the other hand, is special because it requires “manual activities”, i.e., the note can only be implemented after a manual (but minimal) correction.
Collective note 3131047 on the “log4shell” vulnerability
In December 2021 – fitting to the pre-Christmas hustle and bustle – the vulnerability “log4shell ” and its cleanup determined the daily business of many developers, administrators and system managers. Two aspects make this vulnerability special: the wide distribution of the affected component as well as the easy exploitability – the BSI (Federal Office for Information Security) reacted with the “IT threat level: red”2. SAP applications were also widely affected: 21(!) notes about log4shell are included in this collective note.
The vulnerability is in a widely used open-source component for Java applications (log4j) and can be fixed via an update to the latest version. Basically, therefore, a different technology stack (Java) is affected than in the system relevant to this blog (NW-ABAP stack). However, since the vulnerability is highly critical (easy exploitation, wide distribution, large impact), all related advisories were manually checked to confirm that they are not relevant (as expected).
No further necessary activities resulted from the review. Therefore, notes were subsequently set to the processing status “not relevant” and collective note 3131047 was set to “completed”.
This brings us to the end of our first experience report for January. From now on, we will inform you monthly about our experiences and the specifics you should consider when applying the new SAP security patches.
References
1 SAP Security Patch Day: https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=596902035
2 BSI – Schwachstelle Log4Shell: BSI – Presse – Update: Warnstufe Rot: Schwachstelle Log4Shell führt zu extrem kritischer Bedrohungslage (bund.de)