
SAP Security Monitoring & Incident Response Management for
SAP Enterprise Threat Detection
Organizations are facing an increasing number of cyberattacks against their SAP systems, most of the times without even knowing that their data had been compromised. The most effective protection is implementing a SAP Security Monitoring and Incident Response process to be able to identify and mitigate vulnerabilities before they even can be exploited.
Cyberattacks have been rated as one of the Top 5 risks in “The Global Risks Report 2020” by the World Economic Forum, continuing to grow as IoT cyberattacks alone are expected to double by 2025. As a result of the COVID-19 pandemic almost every industry had to implement new solutions quickly (e.g., remote accesses), giving attackers an even bigger surface to act on.
Research states that companies have a big need for action since the rate of detection is only around 0.05%. This means that most of the cyberattacks remain unnoticed, giving hackers plenty of time to explore the landscape and to obtain the data they are looking for. A slow response to a data breach can cause even more trouble for your organization, resulting in a loss of customer trust, productivity, or regulatory fines.
To protect your SAP assets from cyberattacks, we provide advanced services for SAP Security Monitoring & Incident Response Management with SAP Enterprise Threat Detection (ETD):
- SAP Security Monitoring and SIEM-integration
- Incident Response Management
- Advisory and support for mitigation of vulnerabilities
- Forensic analysis
SAP Security Monitoring and SIEM-integration
SAP Security Monitoring is a living process that we operate on a permanent basis. With our specialized monitoring and incident response team, we are able discover threats or suspicious activity (events) inside your SAP landscape and take countermeasures to protect your most valuable business assets – your data.
Through continuous monitoring, our SAP security specialists analyze these events and evaluate whether
Through continuous monitoring with SAP Enterprise Threat Detection (SAP ETD), our SAP security specialists analyze the events (alerts) provided by SAP ETD and assess whether they are authorized accesses or possible security incidents that require countermeasures. Response time is key for us. After the alert has been received by our SAP Security Monitoring Team, process automations come into play, which will be developed during the project based on the history (number of alerts per use case). The development of process automations is an integral part in our way of working in order to avoid as many manual steps as possible.
To successfully integrate SAP Security Monitoring into your IT security processes, we can integrate SAP ETD into your SIEM (Security Information and Event Management) system and build the bridge to your SOC (Security Operation Center). By contributing our SAP Security & Compliance expertise, we are a valuable addition for your SOC to cover all security specifics that come with SAP technology.
Incident Response Management
The key for a successful incident response management is having the right process in place, ideally, enabling the team members to take immediate countermeasures if necessary. The Initial categorization and prioritization of incidents is a critical step for determining how the incident will be handled and how much time is available for its resolution. Following our best practice approach, our incident response management process can be summarized as follows:
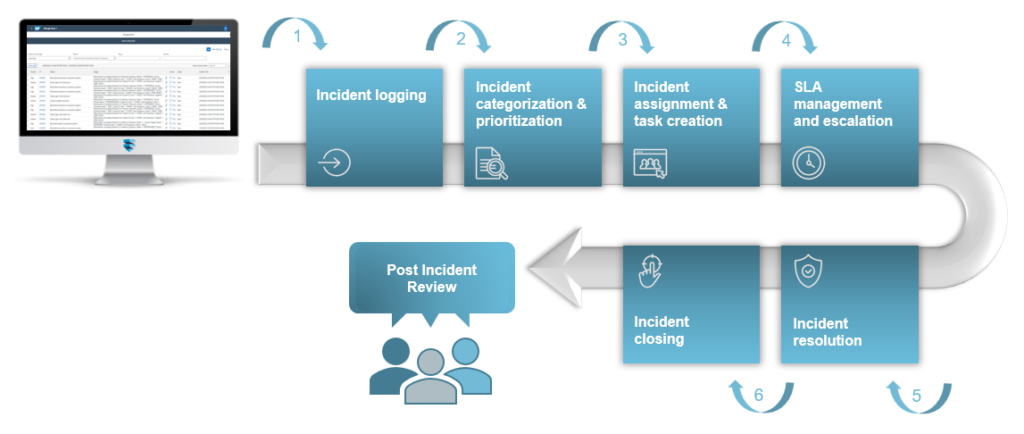
Step 1: Incident logging
In the first step, the alert will be investigated and evaluated to decide whether a ticket will be created directly or whether further investigation needs to be done first. All incidents will be logged and tracked so that a complete historical record is available to provide you with significant information.
Step 2: Incident categorization & prioritization
The incidents will automatically be categorized in the order of criticality to determine the resolution time by using automated ticket rules which save valuable time in the process. The assignment of the right priority to a ticket has a direct impact on the subsequent process of incident analysis.
Step 3: Incident assignment & task creation
Once the incident is categorized and prioritized, it will automatically be assigned to one of our SAP security specialists with the relevant expertise. Based on the complexity of the incident, the countermeasures can be broken down into sub-activities or tasks, if different expertise from multiple specialists is required for further investigation or further action.
Step 4: SLA management and escalation
The response and resolution time is defined in the SLA (Service Level Agreement) which serves as guideline for us to ensure that an incident is processed according to the agreed terms and conditions. If an SLA is breached, we escalate the incident to ensure a fast and prioritized resolution in a common approach with your IT security organization.
Step 5: Incident resolution
We consider an incident to be solved, as soon as our SAP security specialists come up with a temporary workaround or a permanent solution that solves the detected issue.
Step 6: Incident closure
All relevant information and a description of the risk will be documented for the closure of the incident. The incident will be closed in the ticket system as soon as the problem is solved and the solution is accepted by the responsible persons.
Post Incident Review
After an incident is closed, our best practices include documenting all steps taken to resolve the incident and prevent its reoccurrence (if possible). Post Incident Review assists the organization and prepares it for future incidents that follow similar scenarios, resulting in reduced resolution time and a more effective response. Based on the review and documentation, further automations can be developed to standardize the approach to similar incidents.
Advisory and support for mitigation of vulnerabilities
When our monitoring and incident response team discovers threats or suspicious activity, we act quickly to investigate and either work with you on thorough mitigation approaches or take over the mitigation completely. As part of our service, we advise your oranization on taking preventive measures and support the processes for reducing risks. In this way, we improve your security & compliance together every single day.
Forensic analysis
In case your organization had been a victim of a cyberattack, our forensics investigate and document the course, reasons, culprits, and consequences of the security incident or violation of rules of the organization or state laws. Through our experience with SAP attack vectors, we are often able to reconstruct the scenario and provide evidence for further legal action. The only way for organizations to defend themselves is to detect and respond with accuracy and speed.
For detailed insights about our Managed Service, please get in touch with us directly.